The SSL protocol runs above the TCP/IP and below higher-level protocols such as HTTP. It uses TCP/IP on behalf of the higher-level protocols.
The TLS handshake happens after the TCP handshake. For the TCP or for the transport layer, everything in the TLS handshake is just application data. Once the TCP handshake is completed the TLS layer will initiate the TLS handshake.
https secure http
wss secure websocket
refer to 《network.md/tls》
# SSL/TLS Certificate 证书类型
工具:keytool openssl
证书可以单纯只是包含ca认证的证书链(CA的签名)或自签名,以及公钥,也可以同时包含私钥,私钥当然可以独立于证书生成单独存储;
带密码:spring boot mvc程序,这样好处是双重保护,因为需要同时需要密码和私钥才可以
不带密码:ngnix,私钥或者是含有私钥的证书一定要控制读取权限
按照生成方式分为:
# self-sgined certificate
------------------------------------------------------------
--- use openssl 不带密码
------------------------------------------------------------
sudo mkdir /etc/ssl/privatekey
sudo chmod 700 /etc/ssl/privatekey
sudo openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout /etc/ssl/privatekey/nginx-selfsigned.key -out /etc/ssl/certs/nginx-selfsigned.crt
vim nginx-selfsigned.crt
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
vim /etc/ssl/privatekey/nginx-selfsigned.key
-----BEGIN PRIVATE KEY-----
-----END PRIVATE KEY-----
openssl x509 -in nginx-selfsigned.crt -text -noout
keytool -printcert -file /etc/ssl/certs/nginx-selfsigned.crt
检查crt跟private key是否匹配:
openssl x509 -noout -modulus -in test.crt | openssl md5
openssl rsa -noout -modulus -in test.key | openssl md5
两者输出的 Modulus 应该一致(RSA素数乘积,用来生成key pair)
------------------------------------------------------------
--- use keytool 带密码
------------------------------------------------------------
-- Generate a Java keystore and key pair
keytool -genkey -alias mydomain -keyalg RSA -keystore keystore.jks -keysize 2048
-- Generate a certificate signing request (CSR) for an existing Java keystore
keytool -certreq -alias mydomain -keystore keystore.jks -file mydomain.csr
-- Import a root or intermediate CA certificate to an existing Java keystore
keytool -import -trustcacerts -alias root -file Thawte.crt -keystore keystore.jks
-- Import a signed primary certificate to an existing Java keystore
keytool -import -trustcacerts -alias mydomain -file mydomain.crt -keystore keystore.jks
-- Generate a keystore and self-signed certificate
keytool -genkey -keyalg RSA -alias selfsigned -keystore keystore.jks -storepass password -validity 360 -keysize 2048
-- Export a certificate from a keystore
keytool -export -alias selfsigned -file selfsigned.crt -keystore keystore.jks
keytool -genkey -alias secure_netty -keysize 2048 -validity 365 -keyalg RSA -dname "CN=localhost" -keypass 123456 -storepass 123456 -keystore selfsigned.jks
keytool -export -alias secure_netty -keystore selfsigned.jks -storepass 123456 -file selfsigned.cer
keytool -genkey -alias secure_tomcat -keysize 1024 -validity 365 -keyalg RSA -keypass 123456 -storepass 123456 -keystore selfsigned.keystore
keytool -list -v -keystore selfsigned.keystore
打印信息包含 Entry type: PrivateKeyEntry
keytool -export -alias secure_tomcat -keystore selfsigned.keystore -file selfsigned.cer
example:
java import self-signed certificate
keytool.exe -import -trustcacerts -keystore ../lib/security/cacerts -storepass changeit -noprompt -alias myownaliasformysystem -file "\saved-certs\ca.cert"
https://stackoverflow.com/questions/11617210/how-to-properly-import-a-selfsigned-certificate-into-java-keystore-that-is-avail
tomcat:
https://support.microfocus.com/kb/doc.php?id=7022204
# 三方免费证书
# let's encrypt
//自动化工具
wget https://dl.eff.org/certbot-auto
chmod a+x certbot-auto
./certbot-auto certonly --standalone -d www.demoProject.com # www.demoProject.com为你想要配置https的域名
ls /etc/letsencrypt/live/
//证书定时自动更新
crontab -e #编辑crontab
30 2 * * 1 /root/certbot-auto renew --pre-hook "systemctl stop nginx" --post-hook "systemctl start nginx" >> /var/log/le-renew.log 2>&1 &
root/certbot-auto renew --pre-hook "systemctl stop nginx" --post-hook "systemctl start nginx"
# cloudflare dns解析提供商免费证书
cloudflare比较特殊,它提供给了所谓 dns over tls,添加网站到cloudflare并且替换域名商的dns解析为cloudflare之后,dns的解析会被云朵点亮代表收到cloudflare保护 (opens new window); 然后cloudflare提供了几种加密模式,具体参考下面
# Supporting https
# browser
浏览器自然是全面支持https的,不过不同浏览器的特性不同,比如
chrome是采用了操作系统本身的CA证书链,
而firefox是有完整自己的一套证书,所以对于渗透测试者来说,firefox是首选,因为不需要改变操作系统本身的证书,只需要安装给firefox本身就行了,当然firefox还有个特性是支持proxy,chrome还得装插件才行;
注意:如果是自签证书,浏览器会提示,可以手动信任,之后就可以正常访问,但是下面的js http client则不同
访问后端的时候需要注意cors也就是same origin的问题,比如reactjs项目本地测试默认开启nodejs服务:http://localhost:3000,这样访问后端服务,如果后端服务没有设置allow origin,因为后端服务端口一般不会刚好是3000,如果是其他端口,即使也是localhost服务,因为端口不同,不属于same origin,无法请求
# js http client
注意:跟上面不同的是,这里是没有用户交互的,而是js代码自动请求到后端,如果是自签证书,浏览器是不信任的,解决办法就是想办法手动从浏览器地址栏访问一次后端,然后手动加信任,之后应该就可以了,或者另外一种方式是
import axios from 'axios'
import https from 'https'
const result = await axios.post(
`https://${url}/login`,
body,
{
httpsAgent: new https.Agent({
rejectUnauthorized: false
})
}
)
这样会完全忽略证书验证,不太好,所以更好的方法是:
https://stackoverflow.com/questions/51363855/how-to-configure-axios-to-use-ssl-certificate
const httpsAgent = new https.Agent({ ca: MY_CA_BUNDLE });
# nginx
refer to 《buildingblock/nginx.md》
nginx.conf:
server {
listen 80;
listen 443 ssl;
listen [::]:443 ssl;
server_name localhost;
ssl_certificate /etc/ssl/certs/nginx-selfsigned.crt;
ssl_certificate_key /etc/ssl/privatekey/nginx-selfsigned.key;
ssl_dhparam /etc/ssl/certs/dhparam.pem;
# jdk java client
Cacerts are default Trust store provided by every JVM vendor. We will see this cacerts file under JRE/lib/security folder.
如果不导入证书输出错误: trustAnchors parameter must be non-empty or javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No name matching found
keystore 默认密码 changeit
查看/验证
C:\Program Files\Java\jdk1.8.0_231\bin
C:\Program Files\Java\jdk1.8.0_231\jre\lib\security\cacerts
C:\WINDOWS\system32>keytool.exe -list -v -keystore "C:\Program Files\Java\jdk1.8.0_231\jre\lib\security\cacerts"
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains XX entries
Alias name: verisignclass2g2ca [jdk]
Creation date: 25 Aug 2016
Entry type: trustedCertEntry
Owner: OU=VeriSign Trust Network, OU="(c) 1998 VeriSign, Inc. - For authorized use only", OU=Class 2 Public Primary Certification Authority - G2, O="VeriSign, Inc.", C=US
Issuer: OU=VeriSign Trust Network, OU="(c) 1998 VeriSign, Inc. - For authorized use only", OU=Class 2 Public Primary Certification Authority - G2, O="VeriSign, Inc.", C=US
Serial number: b92f60cc889fa17a4609b85b706c8aaf
Valid from: Mon May 18 08:00:00 SRET 1998 until: Wed Aug 02 07:59:59 SRET 2028
Certificate fingerprints:
Signature algorithm name: SHA1withRSA
Subject Public Key Algorithm: 1024-bit RSA key
Version: 1
*******************************************
*******************************************
Alias name: test-selfsigned
Creation date: 25 Oct 2022
Entry type: trustedCertEntry
Owner: CN=test.local, OU=LYHISTORY, O=LYHISTORY, L=SG, ST=SG, C=SG
Issuer: CN=test.local, OU=LYHISTORY, O=LYHISTORY, L=SG, ST=SG, C=SG
Serial number: c79bfcff9e2a5aa77fd103e685f650a825346b9
Valid from: Tue Oct 18 10:50:58 SRET 2022 until: Fri Oct 15 10:50:58 SRET 2032
Certificate fingerprints:
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
导入
C:\Program Files\Java\jdk1.8.0_231\bin>keytool.exe -importcert -file test-selfsigned.crt -keystore "C:\Program Files\Java\jdk1.8.0_231\jre\lib\security\cacerts" -alias "test-selfsigned"
Enter keystore password:
Owner: CN=test.local, OU=LYHISTORY, O=LYHISTORY, L=SG, ST=SG, C=SG
Issuer: CN=test.local, OU=LYHISTORY, O=LYHISTORY, L=SG, ST=SG, C=SG
Serial number: c79bfcff9e2a5aa77fd103e685f650a825346b9
Valid from: Tue Oct 18 10:50:58 SGT 2022 until: Fri Oct 15 10:50:58 SGT 2032
Certificate fingerprints:
Signature algorithm name: SHA256withRSA
Subject Public Key Algorithm: 2048-bit RSA key
Version: 3
Extensions:
Trust this certificate? [no]: yes
Certificate was added to keystore
# springboot mvc
首先MVC有自己的端口比如10001,内置的tomcat默认的http端口是8080,
所有请求到spring mvc这个后台的都是通过 http://IP:10001 过来的,然后内部再交由tomcat 8080端口处理,
如果设置https比如8443,如下:
yml:
#debug: true
server:
servlet:
context-path: /test
port:
10001
ssl:
key-store: selfsigned.keystore
key-store-password: 123456
keyStoreType: JKS
keyAlias: secure_tomcat
@EnableAsync
@SpringBootApplication
public class Application {
public static void main(String[] args) {
SpringApplication.run(Application.class, args);
}
@Bean
public RestTemplate restTemplate() {
return new RestTemplate();
}
/**
* http重定向到https
* @return
*/
@Bean
public TomcatServletWebServerFactory servletContainer() {
TomcatServletWebServerFactory tomcat = new TomcatServletWebServerFactory() {
@Override
protected void postProcessContext(Context context) {
SecurityConstraint constraint = new SecurityConstraint();
constraint.setUserConstraint("CONFIDENTIAL");
SecurityCollection collection = new SecurityCollection();
collection.addPattern("/*");
constraint.addCollection(collection);
context.addConstraint(constraint);
}
};
//这里tomcat.getPort拿到的就是8080
tomcat.addAdditionalTomcatConnectors(httpConnector(tomcat.getPort()));
return tomcat;
}
@Bean
public Connector httpConnector(int port) {
Connector connector = new Connector("org.apache.coyote.http11.Http11NioProtocol");
connector.setScheme("http");
//Connector监听的http的端口号
connector.setPort(port);
connector.setSecure(false);
//监听到http的端口号后转向到的https的端口号
connector.setRedirectPort(8443);
return connector;
}
}
注意到上面server本身就监听10001(应该是内置tomcat监听),然后为了https,需要创建tomcatfatory又出现一个http端口8080,为什么不可以直接扩展或override postProcessContext方法,可能是跟整个spring mvc的生命周期启动过程相关:
https://zhuanlan.zhihu.com/p/81807865
# netty
https://blog.csdn.net/invadersf/article/details/80337380
https://www.cnblogs.com/zhjh256/p/6488668.html
import io.netty.handler.ssl.SslHandler;
public class SslChannelInitializer extends ChannelInitializer<Channel> {
private final SslContext context;
public SslChannelInitializer(SslContext context) {
this.context = context;
}
@Override
protected void initChannel(Channel ch) throws Exception {
SSLEngine engine = context.newEngine(ch.alloc());
engine.setUseClientMode(false);
ch.pipeline().addFirst("ssl", new SslHandler(engine));
ChannelPipeline pipeline = ch.pipeline();
pipeline.addLast("frameDecoder", new LengthFieldBasedFrameDecoder(Integer.MAX_VALUE, 0, 4, 0, 4));
pipeline.addLast("frameEncoder", new LengthFieldPrepender(4));
pipeline.addLast("decoder", new StringDecoder(Charset.forName("UTF-8")));
pipeline.addLast("encoder", new StringEncoder(Charset.forName("UTF-8")));
pipeline.addLast("spiderServerBusiHandler", new SpiderServerBusiHandler());
}
}
bossGroup = new NioEventLoopGroup(1);
workerGroup = new NioEventLoopGroup(WORKER_GROUP_SIZE);
channelClass = NioServerSocketChannel.class;
logger.info("workerGroup size:" + WORKER_GROUP_SIZE);
logger.info("preparing to start spider server...");
b.group(bossGroup, workerGroup);
b.channel(channelClass);
KeyManagerFactory keyManagerFactory = null;
KeyStore keyStore = KeyStore.getInstance("JKS");
keyStore.load(new FileInputStream("selfsigned.jks"), "sNetty".toCharArray());
keyManagerFactory = KeyManagerFactory.getInstance("SunX509");
keyManagerFactory.init(keyStore,"123456".toCharArray());
SslContext sslContext = SslContextBuilder.forServer(keyManagerFactory).build();
b.childHandler(new SslChannelInitializer(sslContext));
# 案例 Use Case 1: client-server
这里的client就是浏览器或手机端,
这里的server指的是前后端代码集成一起的后端服务,
比较直白,只有两方参与,浏览器不需要什么设置,后端服务如果是self host则需要其本身实现https,比如spring mvc,如果不是self host,而是host在比如nginx或iis中,则需要对nginx或iis配置https支持即可;
# 案例 Use Case 2: client-cdn-server
example: 网站使用cloudflare的证书
Cloudflare 提供几种模式 Encryption modes:
- flexible allows HTTPS connections between your visitor and Cloudflare, but all connections between Cloudflare and your origin are made through HTTP. As a result, an SSL certificate is not required on your origin. 这种模式 server端无需配置tls
- full
Cloudflare allows HTTPS connections between your visitor and Cloudflare and makes connections to the origin using the scheme requested by the visitor. If your visitor uses http, then Cloudflare connects to the origin using plaintext HTTP and vice versa.
这种模式 server端可以配置
- self-signed 自签证书
- Cloudflare Origin CA,Cloudflare Origin Certificate 是一个只被 Cloudflare 信任的证书,不被浏览器所信任,所以使用「Cloudflare Origin Certificate」就必须在前面使用 Cloudflare 添加 DNS 记录时将云朵点亮,即 ☁ Proxied。如果不点亮云朵,您的网站将无法安全访问,同时代理也会无法正常连接。 (opens new window)
- or purchased from a Certificate Authority)
- full(strict) Cloudflare does everything in Full mode but also enforces more stringent requirements for origin certificates. 这种模式server端需要使用cloudflare认可的证书:
# 配置例子:client->cloudflare->server, full strict模式并开启authenticated origin pulls
Cloudflare’s Origin CA生成: cloudflare管理页面=>SSL/TLS=>Origin Server点击生成证书; 保存证书至 /etc/ssl/cloudflare_cert.pem 保存key至 /etc/ssl/cloudflare_key.pem
SSL/TLS 加密模式改为 Full (strict)
Edge Certificates=>Minimum TLS Version」改为「TLS 1.2」
Enable authenticated origin pulls 如果在 Nginx 服务器上设置了「Authenticated Origin Pulls」,就可以确保它只接受来自 Cloudflare 服务器的请求,防止任何其他人直接连接到 Nginx 服务器, cloudflare管理页面=>SSL/TLS=>Origin Server,打开「Authenticated Origin Pulls」 。
然后访问该页面 (opens new window),可以找到下载client证书链接: download authenticated_origin_pull_ca.pem (opens new window) 将证书 authenticated_origin_pull_ca.pem 的内容写入到服务器的 /etc/ssl/cloudflare_client.crt 中
nginx 配置:
server { listen 443 ssl http2; listen [::]:443 ssl http2; ssl_certificate /etc/ssl/cert.pem; ssl_certificate_key /etc/ssl/key.pem; ssl_client_certificate /etc/ssl/cloudflare_client.crt; ssl_verify_client on; ssl_session_timeout 1d; ssl_session_cache shared:MozSSL:10m; # about 40000 sessions ssl_session_tickets off; # intermediate configuration ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384; ssl_prefer_server_ciphers off; # HSTS (ngx_http_headers_module is required) (63072000 seconds) add_header Strict-Transport-Security "max-age=63072000" always;
# 案例 Use Case 2: separated frontend/backend前后端分离
举例前后端分离项目: 1.(user interact ) browser request nginx for frontend resource create self-signed cert and config nignx, so browser will talk to nginx through https (unsafe warning will be alert as it's self signed)
2.(no user interact) js codes will make http call to backend service to retrieve data through nginx, nginx forward http request to backend service backend service has to implement and support https, and nginx also have to act as a https client to handshake with the backend service
3.(no user interact) js codes will connect to websocket server directly
假设前端项目用的是create-reactjs-app脚手架,npm run start会开启一个nodejs服务,如下
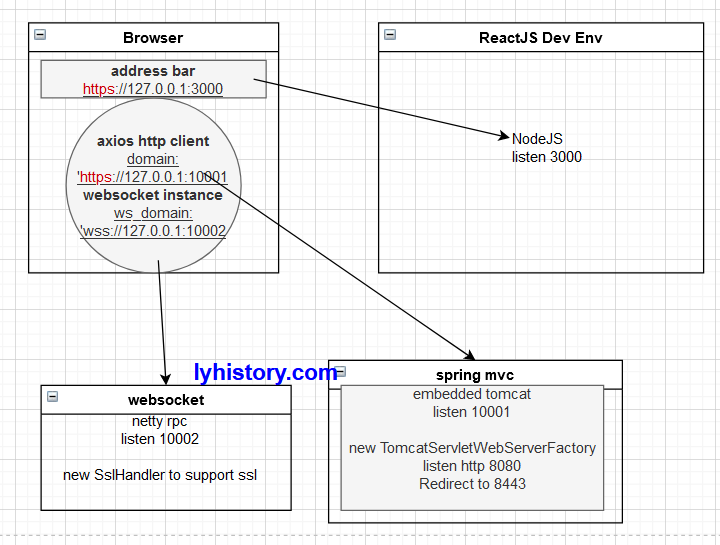
这种情况下显然是不可行的,首先:
1.默认情况下,origin是https://127.0.0.1:3000,axios http client请求的host是 https://127.0.0.1:10001 ,会被same origin policy阻挡,
注意如果是<img src=https://127.0.0.1:3000/verifycode 这种图片src的验证码是不会被block住的,因为img link script等标签不会受制于same origin policy
2.浏览器用户互动的部分请求到的host是nodejs,而非用户互动的axios请求到的host是spring mvc,因为开发环境肯定都是自签证书,即使给nodejs设置好了自签证书,浏览器第一次会提醒用户不安全,用户选择继续访问后浏览器则记住该证书,但是axios请求的是spring mvc程序的证书,跟nodejs一般是不同的,这种情况下就会有问题
1的一个解决办法是通过设置chrome浏览器,允许其跨域: https://segmentfault.com/a/1190000021711445
2的一个解决方法是nodejs跟spring mvc用相同的证书,或者手动给浏览器安装证书:https://qastack.cn/superuser/27268/how-do-i-disable-the-warning-chrome-gives-if-a-security-certificate-is-not-trusted
但是其实更完美的解决方法是加一个nginx,nginx作为proxy转发两者的流量到nodejs和springmvc,这样浏览器本身和其中的js代码axios http client只需要跟nginx进行handshake即可,而且origin和host都是test.local,不存在跨域问题,参考下面这张图:
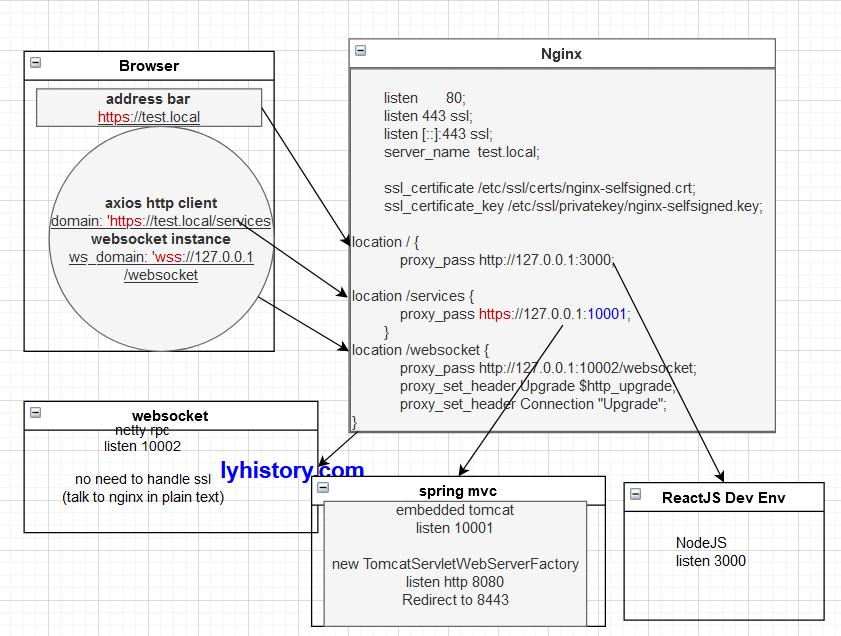
注意,关于websocket有两点:
如果网站使用了https,默认必须使用wss,ws会被浏览器block住,另外注意到,这里前端跟nginx之间是使用wss的,nginx跟真正的服务端仍然是明文ws通信,这个很正常,本来nginx就是反向代理,客户端不需要直接跟被代理的服务端连接,所以实际上同理后端的服务也可以只用http跟nginx通信;
如果是本地测试 127.0.0.1,特别要小心,如图域名使用test.local会出现问题:provisional headers are shown
解决办法是,nginx将server_name改为localhost即可
而最终部署到服务器上则会简化,因为就不需要nodejs开发环境了:
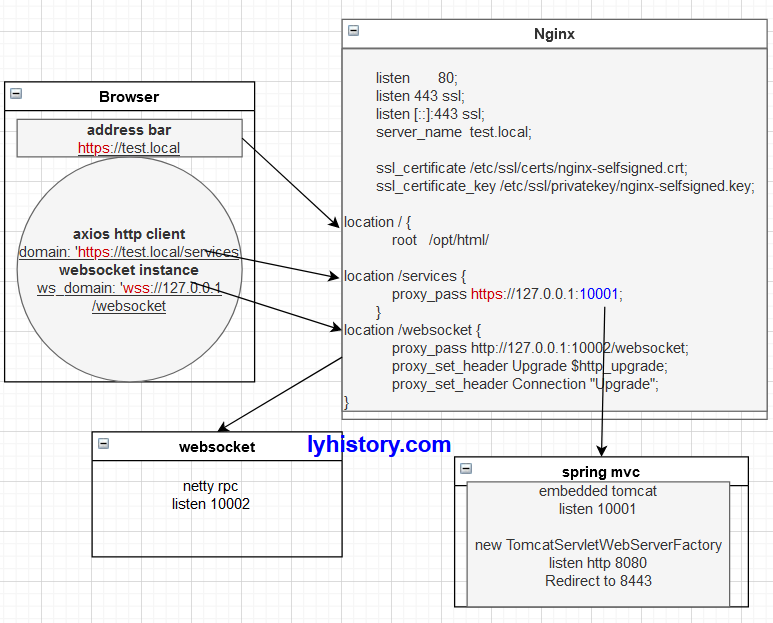
测试完https后,想回去测试http,chrome经常会强制使用https,解决办法:
https://superuser.com/questions/565409/how-to-stop-an-automatic-redirect-from-http-to-https-in-chrome
- Go to
chrome://net-internals/#hsts. Enter 3rdrevolution.com under Delete domain security policies and press the Delete button. - Now go to
chrome://settings/clearBrowserData, tick the box Cached images and files and press click the button Clear data.
# Troubleshooting
# 查看服务器支持的TLS版本
nmap -p 443 --script ssl-enum-ciphers <TARGET>
openssl s_client -host api.compass-ft.com -port 443
# 查看服务器支持的cipher suite
To get a list of all cipher suites supported by your installation of OpenSSL, use the openssl command with the ciphers subcommand as follows:
$ openssl ciphers -v 'ALL:COMPLEMENTOFALL'
to only list suites that are defined as belonging to the HIGH group, use the following command:
$ openssl ciphers -v 'HIGH'
https://www.keyfactor.com/blog/cipher-suites-explained/
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
Key Exchange - Authentication - Cipher(algorithm, strength, mode) - Hash or MAC
# NET::ERR_CERT_COMMON_NAME_INVALID
如果是设置,基本就是域名跟证书不一致,比如证书中的:
openssl x509 -noout -text -in test.crt
Subject: CN = *.test.com
nginx配置的server_name就需要是其子域名
如果是访问其他网站遇到,可能是dns解析问题:
https://blog.csdn.net/zerooffdate/article/details/80513730
# SSL_CTX_use_PrivateKey failed
emerg] SSL_CTX_use_PrivateKey failed (SSL: error:0B080074:x509 certificate routines:X509_check_private_key:key values mismatch)
私钥和证书不匹配,验证
openssl x509 -noout -modulus -in certificate.crt | openssl md5
openssl rsa -noout -modulus -in privateKey.key | openssl md5
# 服务端cert过期导致Handshake请求失败
sprintboot访问一个https的api遇到问题:
2022-01-25 16:18:05.175 ^[[31mERROR^[[m ^[[35m30604GG^[[m [scheduling-1] ^[[36mc.a.m.f.u.HttpClientUtil^[[m : Get Exception Remote host closed connection during handshake
javax.net.ssl.SSLHandshakeException: Remote host closed connection during handshake
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:980)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1363)
at sun.security.ssl.SSLSocketImpl.writeRecord(SSLSocketImpl.java:735)
at sun.security.ssl.AppOutputStream.write(AppOutputStream.java:123)
at java.io.BufferedOutputStream.flushBuffer(BufferedOutputStream.java:82)
at java.io.BufferedOutputStream.flush(BufferedOutputStream.java:140)
at org.apache.commons.httpclient.HttpConnection.flushRequestOutputStream(HttpConnection.java:828)
at org.apache.commons.httpclient.HttpMethodBase.writeRequest(HttpMethodBase.java:2116)
at org.apache.commons.httpclient.HttpMethodBase.execute(HttpMethodBase.java:1096)
at org.apache.commons.httpclient.HttpMethodDirector.executeWithRetry(HttpMethodDirector.java:398)
at org.apache.commons.httpclient.HttpMethodDirector.executeMethod(HttpMethodDirector.java:171)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:397)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:323)
at com.lyhistory.middleware.test.util.HttpClientUtil.sendGet(HttpClientUtil.java:64)
at com.lyhistory.middleware.test.service.impl.CompassftServiceImpl.sendRequest(CompassftServiceImpl.java:25)
at com.lyhistory.middleware.test.job.CompassftJob.crawlData(CompassftJob.java:33)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:497)
at org.springframework.scheduling.support.ScheduledMethodRunnable.run(ScheduledMethodRunnable.java:84)
at org.springframework.scheduling.support.DelegatingErrorHandlingRunnable.run(DelegatingErrorHandlingRunnable.java:54)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.runAndReset(FutureTask.java:308)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$301(ScheduledThreadPoolExecutor.java:180)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:294)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at java.lang.Thread.run(Thread.java:745)
Caused by: java.io.EOFException: SSL peer shut down incorrectly
at sun.security.ssl.InputRecord.read(InputRecord.java:505)
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:961)
... 28 more
但是此前在另外一台服务器上测试没有问题,确定了浏览器访问该api没有问题,然后在这台机器上curl一下
#curl https://api.compass-ft.com/v1/indexes/CCRTBTC/history?access_token=
curl: (60) The certificate issuer's certificate has expired. Check your system date and time.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
说是证书过期,浏览器查看一下果然过期了几天,可能是浏览器不会那么频繁的验证,在此前另外一台装好的机器上curl没问题,估计是首次访问才验证,后续就验证了或者定期检查,
通知api提供商,提供商迅速更新了证书,浏览器看了下,确实更新了,postman也能访问,但是这台机器上仍然无法访问,curl也是一样的提示,
根据curl的提示查看
https://curl.se/docs/sslcerts.html
openssl s_client -showcerts -servername server -connect server:443 > cacert.pem- type "quit", followed by the "ENTER" key
- The certificate will have "BEGIN CERTIFICATE" and "END CERTIFICATE" markers.
- If you want to see the data in the certificate, you can do: "openssl x509 -inform PEM -in certfile -text -out certdata" where certfile is the cert you extracted from logfile. Look in certdata.
结合这个帖子 https://stackoverflow.com/questions/24992976/openssl-telling-certificate-has-expired-when-it-has-not
openssl s_client -showcerts -servername api.compass-ft.com -connect api.compass-ft.com:443
CONNECTED(00000003)
depth=3 O = Digital Signature Trust Co., CN = DST Root CA X3
verify error:num=10:certificate has expired
notAfter=Sep 30 14:01:15 2021 GMT
verify return:0
---
Certificate chain
0 s:/CN=api.compass-ft.com
i:/C=US/O=Let's Encrypt/CN=R3
-----BEGIN CERTIFICATE-----
#openssl s_client -servername api.compass-ft.com -connect api.compass-ft.com:443
CONNECTED(00000003)
depth=3 O = Digital Signature Trust Co., CN = DST Root CA X3
verify error:num=10:certificate has expired
notAfter=Sep 30 14:01:15 2021 GMT
verify return:0
---
Certificate chain
0 s:/CN=api.compass-ft.com
i:/C=US/O=Let's Encrypt/CN=R3
1 s:/C=US/O=Let's Encrypt/CN=R3
i:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
2 s:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
---
Server certificate
-----BEGIN CERTIFICATE-----
openssl s_client -servername api.compass-ft.com -connect api.compass-ft.com:443 2>/dev/null | openssl x509 -noout -dates
又从浏览器观察了这三级的证书链,都是正常的,所以怀疑是os上的根证书链中哪个可能过期了但一直没更新!
]#find / -type d -name "certs"
/etc/pki/CA/certs
/etc/pki/tls/certs
/etc/openldap/certs
#openssl x509 -in ca-bundle.crt -text
openssl x509 -enddate -noout -in
#curl -v https://api.compass-ft.com/v1/indexes/
* About to connect() to api.compass-ft.com port 443 (#0)
* Trying 54.216.252.255...
* Connected to api.compass-ft.com (54.216.252.255) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* Server certificate:
* subject: CN=api.compass-ft.com
* start date: Dec 09 23:25:14 2021 GMT
* expire date: Mar 09 23:25:13 2022 GMT
* common name: api.compass-ft.com
* issuer: CN=R3,O=Let's Encrypt,C=US
* NSS error -8162 (SEC_ERROR_EXPIRED_ISSUER_CERTIFICATE)
* The certificate issuer's certificate has expired. Check your system date and time.
* Closing connection 0
curl: (60) The certificate issuer's certificate has expired. Check your system date and time.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
搜索得知:
For TLS certificates issued by Let’s Encrypt, the root certificate (DST Root CA X3) in the default chain expires on ***September 30, 2021***.
https://blog.devgenius.io/rhel-centos-7-fix-for-lets-encrypt-change-8af2de587fe4
插曲:开始还一度怀疑是不是os支持的tls Protocol跟api服务商支持的不同
openssl ciphers -v | awk '{print $2}' | sort | uniq
# jdk版本bug导致Handshake失败
跟前面一样dev上可以,生产上失败,错误输出也一样
2022-01-27 17:45:29.928 ^[[31mERROR^[[m ^[[35m25521GG^[[m [scheduling-1] ^[[36mc.a.m.f.u.HttpClientUtil^[[m : Get Exception Remote host closed connection during handshake
javax.net.ssl.SSLHandshakeException: Remote host closed connection during handshake
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:980)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1363)
at sun.security.ssl.SSLSocketImpl.writeRecord(SSLSocketImpl.java:735)
at sun.security.ssl.AppOutputStream.write(AppOutputStream.java:123)
at java.io.BufferedOutputStream.flushBuffer(BufferedOutputStream.java:82)
at java.io.BufferedOutputStream.flush(BufferedOutputStream.java:140)
at org.apache.commons.httpclient.HttpConnection.flushRequestOutputStream(HttpConnection.java:828)
at org.apache.commons.httpclient.HttpMethodBase.writeRequest(HttpMethodBase.java:2116)
at org.apache.commons.httpclient.HttpMethodBase.execute(HttpMethodBase.java:1096)
at org.apache.commons.httpclient.HttpMethodDirector.executeWithRetry(HttpMethodDirector.java:398)
at org.apache.commons.httpclient.HttpMethodDirector.executeMethod(HttpMethodDirector.java:171)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:397)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:323)
at com.lyhistory.middleware.test.util.HttpClientUtil.sendGet(HttpClientUtil.java:64)
at com.lyhistory.middleware.test.service.impl.CompassftServiceImpl.sendRequest(CompassftServiceImpl.java:25)
at com.lyhistory.middleware.test.job.CompassftJob.crawlData(CompassftJob.java:33)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:497)
at org.springframework.scheduling.support.ScheduledMethodRunnable.run(ScheduledMethodRunnable.java:84)
at org.springframework.scheduling.support.DelegatingErrorHandlingRunnable.run(DelegatingErrorHandlingRunnable.java:54)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.runAndReset(FutureTask.java:308)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$301(ScheduledThreadPoolExecutor.java:180)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:294)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at java.lang.Thread.run(Thread.java:745)
Caused by: java.io.EOFException: SSL peer shut down incorrectly
at sun.security.ssl.InputRecord.read(InputRecord.java:505)
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:961)
... 28 more
通过这个帖子的提示https://stackoverflow.com/questions/21245796/javax-net-ssl-sslhandshakeexception-remote-host-closed-connection-during-handsh
# 进行debug输出更详细的handshake握手内容
[root@sgtcs-mdw-v02 test-datasource]# java -jar -Djavax.net.debug=all test-datasource.jar
2022-01-28 09:11:49,757 main INFO Log4j appears to be running in a Servlet environment, but there's no log4j-web module available. If you want better web container support, please add the log4j-web JAR to your web archive or server lib directory.
2022-01-28 09:11:49,766 main INFO jar:file:/opt/test-datasource/test-datasource.jar!/BOOT-INF/classes!/log4j2.yml does not support dynamic reconfiguration
. ____ _ __ _ _
/\\ / ___'_ __ _ _(_)_ __ __ _ \ \ \ \
( ( )\___ | '_ | '_| | '_ \/ _` | \ \ \ \
\\/ ___)| |_)| | | | | || (_| | ) ) ) )
' |____| .__|_| |_|_| |_\__, | / / / /
=========|_|==============|___/=/_/_/_/
:: Spring Boot :: (v2.4.5)
2022-01-28 09:11:49.871 INFO 23127GG [kground-preinit] o.h.v.i.u.Version : HV000001: Hibernate Validator 6.1.7.Final
2022-01-28 09:11:49.918 INFO 23127GG [main] o.s.b.StartupInfoLogger : Starting testMain v0.0.1-SNAPSHOT using Java 1.8.0_40 on sgtcs-mdw-v02 with PID 23127 (/opt/test-datasource/test-datasource.jar started by root in /opt/test-datasource)
2022-01-28 09:11:49.926 INFO 23127GG [main] o.s.b.SpringApplication : The following profiles are active: datasource
2022-01-28 09:11:51.084 INFO 23127GG [main] o.s.b.w.e.t.TomcatWebServer : Tomcat initialized with port(s): 10999 (http)
2022-01-28 09:11:51.109 INFO 23127GG [main] o.a.j.l.DirectJDKLog : Initializing ProtocolHandler ["http-nio-10999"]
2022-01-28 09:11:51.110 INFO 23127GG [main] o.a.j.l.DirectJDKLog : Starting service [Tomcat]
2022-01-28 09:11:51.110 INFO 23127GG [main] o.a.j.l.DirectJDKLog : Starting Servlet engine: [Apache Tomcat/9.0.45]
2022-01-28 09:11:51.170 INFO 23127GG [main] o.a.j.l.DirectJDKLog : Initializing Spring embedded WebApplicationContext
2022-01-28 09:11:51.171 INFO 23127GG [main] w.s.c.ServletWebServerApplicationContext : Root WebApplicationContext: initialization completed in 1197 ms
2022-01-28 09:11:51.658 INFO 23127GG [main] o.s.s.c.ExecutorConfigurationSupport : Initializing ExecutorService 'applicationTaskExecutor'
2022-01-28 09:11:51.853 INFO 23127GG [main] o.s.s.c.ExecutorConfigurationSupport : Initializing ExecutorService 'taskScheduler'
2022-01-28 09:11:51.884 INFO 23127GG [main] o.a.j.l.DirectJDKLog : Starting ProtocolHandler ["http-nio-10999"]
2022-01-28 09:11:51.907 INFO 23127GG [main] o.s.b.w.e.t.TomcatWebServer : Tomcat started on port(s): 10999 (http) with context path '/middleware'
2022-01-28 09:11:51.922 INFO 23127GG [scheduling-1] c.a.m.f.j.CompassftJob : CompassftJob crawlData, start time is 09:11:51
2022-01-28 09:11:51.924 INFO 23127GG [main] o.s.b.StartupInfoLogger : Started testMain in 2.449 seconds (JVM running for 3.494)
keyStore is :
keyStore type is : jks
keyStore provider is :
init keystore
init keymanager of type SunX509
trustStore is: /apps/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts
trustStore type is : jks
trustStore provider is :
init truststore
trigger seeding of SecureRandom
done seeding SecureRandom
Ignoring unavailable cipher suite: TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_RSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_RSA_WITH_AES_256_CBC_SHA256
Ignoring unavailable cipher suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
Ignoring unavailable cipher suite: TLS_RSA_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
Ignoring unavailable cipher suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
Ignoring unavailable cipher suite: TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
Ignoring unavailable cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
Ignoring unavailable cipher suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
Ignoring unavailable cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
Ignoring unavailable cipher suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
Ignoring unavailable cipher suite: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
Allow unsafe renegotiation: false
Allow legacy hello messages: true
Is initial handshake: true
Is secure renegotiation: false
scheduling-1, setSoTimeout(0) called
scheduling-1, setSoTimeout(60000) called
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 for TLSv1.1
%% No cached client session
*** ClientHello, TLSv1.2
RandomCookie: GMT: 1626554840 bytes = { 233, 246, 57, 123, 111, 81, 50, 152, 19, 185, 227, 133, 240, 86, 55, 133, 151, 4, 29, 231, 232, 156, 23, 144, 11, 15, 125, 61 }
Session ID: {}
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_ECDSA_WITH_RC4_128_SHA, TLS_ECDHE_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_SHA, TLS_ECDH_ECDSA_WITH_RC4_128_SHA, TLS_ECDH_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_MD5, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
Extension elliptic_curves, curve names: {secp256r1, sect163k1, sect163r2, secp192r1, secp224r1, sect233k1, sect233r1, sect283k1, sect283r1, secp384r1, sect409k1, sect409r1, secp521r1, sect571k1, sect571r1, secp160k1, secp160r1, secp160r2, sect163r1, secp192k1, sect193r1, sect193r2, secp224k1, sect239k1, secp256k1}
Extension ec_point_formats, formats: [uncompressed]
Extension signature_algorithms, signature_algorithms: SHA512withECDSA, SHA512withRSA, SHA384withECDSA, SHA384withRSA, SHA256withECDSA, SHA256withRSA, SHA224withECDSA, SHA224withRSA, SHA1withECDSA, SHA1withRSA, SHA1withDSA, MD5withRSA
***
[write] MD5 and SHA1 hashes: len = 207
0000: 01 00 00 CB 03 03 61 F3 42 D8 E9 F6 39 7B 6F 51 ......a.B...9.oQ
0010: 32 98 13 B9 E3 85 F0 56 37 85 97 04 1D E7 E8 9C 2......V7.......
0020: 17 90 0B 0F 7D 3D 00 00 46 C0 23 C0 27 00 3C C0 .....=..F.#.'.<.
0030: 25 C0 29 00 67 00 40 C0 09 C0 13 00 2F C0 04 C0 %.).g.@...../...
0040: 0E 00 33 00 32 C0 2B C0 2F 00 9C C0 2D C0 31 00 ..3.2.+./...-.1.
0050: 9E 00 A2 C0 08 C0 12 00 0A C0 03 C0 0D 00 16 00 ................
0060: 13 C0 07 C0 11 00 05 C0 02 C0 0C 00 04 00 FF 01 ................
0070: 00 00 5C 00 0A 00 34 00 32 00 17 00 01 00 03 00 ..\...4.2.......
0080: 13 00 15 00 06 00 07 00 09 00 0A 00 18 00 0B 00 ................
0090: 0C 00 19 00 0D 00 0E 00 0F 00 10 00 11 00 02 00 ................
00A0: 12 00 04 00 05 00 14 00 08 00 16 00 0B 00 02 01 ................
00B0: 00 00 0D 00 1A 00 18 06 03 06 01 05 03 05 01 04 ................
00C0: 03 04 01 03 03 03 01 02 03 02 01 02 02 01 01 ...............
scheduling-1, WRITE: TLSv1.2 Handshake, length = 207
[Raw write]: length = 212
0000: 16 03 03 00 CF 01 00 00 CB 03 03 61 F3 42 D8 E9 ...........a.B..
0010: F6 39 7B 6F 51 32 98 13 B9 E3 85 F0 56 37 85 97 .9.oQ2......V7..
0020: 04 1D E7 E8 9C 17 90 0B 0F 7D 3D 00 00 46 C0 23 ..........=..F.#
0030: C0 27 00 3C C0 25 C0 29 00 67 00 40 C0 09 C0 13 .'.<.%.).g.@....
0040: 00 2F C0 04 C0 0E 00 33 00 32 C0 2B C0 2F 00 9C ./.....3.2.+./..
0050: C0 2D C0 31 00 9E 00 A2 C0 08 C0 12 00 0A C0 03 .-.1............
0060: C0 0D 00 16 00 13 C0 07 C0 11 00 05 C0 02 C0 0C ................
0070: 00 04 00 FF 01 00 00 5C 00 0A 00 34 00 32 00 17 .......\...4.2..
0080: 00 01 00 03 00 13 00 15 00 06 00 07 00 09 00 0A ................
0090: 00 18 00 0B 00 0C 00 19 00 0D 00 0E 00 0F 00 10 ................
00A0: 00 11 00 02 00 12 00 04 00 05 00 14 00 08 00 16 ................
00B0: 00 0B 00 02 01 00 00 0D 00 1A 00 18 06 03 06 01 ................
00C0: 05 03 05 01 04 03 04 01 03 03 03 01 02 03 02 01 ................
00D0: 02 02 01 01 ....
scheduling-1, received EOFException: error
scheduling-1, handling exception: javax.net.ssl.SSLHandshakeException: Remote host closed connection during handshake
scheduling-1, SEND TLSv1.2 ALERT: fatal, description = handshake_failure
scheduling-1, WRITE: TLSv1.2 Alert, length = 2
[Raw write]: length = 7
0000: 15 03 03 00 02 02 28 ......(
scheduling-1, called closeSocket()
scheduling-1, called close()
scheduling-1, called closeInternal(true)
scheduling-1, called close()
scheduling-1, called closeInternal(true)
scheduling-1, called close()
scheduling-1, called closeInternal(true)
2022-01-28 09:11:52.563 ERROR 23127GG [scheduling-1] c.a.m.f.u.HttpClientUtil : Get Exception Remote host closed connection during handshake
javax.net.ssl.SSLHandshakeException: Remote host closed connection during handshake
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:980)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1363)
at sun.security.ssl.SSLSocketImpl.writeRecord(SSLSocketImpl.java:735)
at sun.security.ssl.AppOutputStream.write(AppOutputStream.java:123)
at java.io.BufferedOutputStream.flushBuffer(BufferedOutputStream.java:82)
at java.io.BufferedOutputStream.flush(BufferedOutputStream.java:140)
at org.apache.commons.httpclient.HttpConnection.flushRequestOutputStream(HttpConnection.java:828)
at org.apache.commons.httpclient.HttpMethodBase.writeRequest(HttpMethodBase.java:2116)
at org.apache.commons.httpclient.HttpMethodBase.execute(HttpMethodBase.java:1096)
at org.apache.commons.httpclient.HttpMethodDirector.executeWithRetry(HttpMethodDirector.java:398)
at org.apache.commons.httpclient.HttpMethodDirector.executeMethod(HttpMethodDirector.java:171)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:397)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:323)
at com.lyhistory.middleware.test.util.HttpClientUtil.sendGet(HttpClientUtil.java:64)
at com.lyhistory.middleware.test.service.impl.CompassftServiceImpl.sendRequest(CompassftServiceImpl.java:25)
at com.lyhistory.middleware.test.job.CompassftJob.crawlData(CompassftJob.java:33)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:497)
at org.springframework.scheduling.support.ScheduledMethodRunnable.run(ScheduledMethodRunnable.java:84)
at org.springframework.scheduling.support.DelegatingErrorHandlingRunnable.run(DelegatingErrorHandlingRunnable.java:54)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.runAndReset(FutureTask.java:308)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$301(ScheduledThreadPoolExecutor.java:180)
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:294)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at java.lang.Thread.run(Thread.java:745)
Caused by: java.io.EOFException: SSL peer shut down incorrectly
at sun.security.ssl.InputRecord.read(InputRecord.java:505)
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:961)
... 28 more
2022-01-28 09:11:52.565 WARN 23127GG [scheduling-1] c.a.m.f.s.i.CompassftServiceImpl : Failed http request to https://api.compass-ft.com/v1/indexes/CCRTBTC/history?access_token=
2022-01-28 09:11:52.565 INFO 23127GG [scheduling-1] c.a.m.f.j.CompassftJob : CompassftJob crawlData, end time is 09:11:52
^C2022-01-28 09:11:57.032 INFO 23127GG [extShutdownHook] o.s.s.c.ExecutorConfigurationSupport : Shutting down ExecutorService 'taskScheduler'
2022-01-28 09:11:57.033 INFO 23127GG [extShutdownHook] o.s.s.c.ExecutorConfigurationSupport : Shutting down ExecutorService 'applicationTaskExecutor'
2022-01-28 09:11:57.034 INFO 23127GG [extShutdownHook] c.a.d.p.DruidDataSource : {dataSource-0} closing ...
# 对比下dev环境成功的输出
[root@os-node3 test-datasource]# java -jar -Djavax.net.debug=all test-datasource.jar
2022-01-28 10:45:45,321 main INFO Log4j appears to be running in a Servlet environment, but there's no log4j-web module available. If you want better web container support, please add the log4j-web JAR to your web archive or server lib directory.
2022-01-28 10:45:45,337 main INFO jar:file:/opt/test-datasource/test-datasource.jar!/BOOT-INF/classes!/log4j2.yml does not support dynamic reconfiguration
. ____ _ __ _ _
/\\ / ___'_ __ _ _(_)_ __ __ _ \ \ \ \
( ( )\___ | '_ | '_| | '_ \/ _` | \ \ \ \
\\/ ___)| |_)| | | | | || (_| | ) ) ) )
' |____| .__|_| |_|_| |_\__, | / / / /
=========|_|==============|___/=/_/_/_/
:: Spring Boot :: (v2.4.5)
2022-01-28 10:45:45.398 INFO 7939GG [kground-preinit] o.h.v.i.u.Version : HV000001: Hibernate Validator 6.1.7.Final
2022-01-28 10:45:45.449 INFO 7939GG [main] o.s.b.StartupInfoLogger : Starting testMain v0.0.1-SNAPSHOT using Java 1.8.0_191 on os-node3 with PID 7939 (/opt/test-datasource/test-datasource.jar started by root in /opt/test-datasource)
2022-01-28 10:45:45.453 INFO 7939GG [main] o.s.b.SpringApplication : The following profiles are active: datasource
2022-01-28 10:45:46.738 INFO 7939GG [main] o.s.b.w.e.t.TomcatWebServer : Tomcat initialized with port(s): 10999 (http)
2022-01-28 10:45:46.759 INFO 7939GG [main] o.a.j.l.DirectJDKLog : Initializing ProtocolHandler ["http-nio-10999"]
2022-01-28 10:45:46.759 INFO 7939GG [main] o.a.j.l.DirectJDKLog : Starting service [Tomcat]
2022-01-28 10:45:46.760 INFO 7939GG [main] o.a.j.l.DirectJDKLog : Starting Servlet engine: [Apache Tomcat/9.0.45]
2022-01-28 10:45:46.814 INFO 7939GG [main] o.a.j.l.DirectJDKLog : Initializing Spring embedded WebApplicationContext
2022-01-28 10:45:46.815 INFO 7939GG [main] w.s.c.ServletWebServerApplicationContext : Root WebApplicationContext: initialization completed in 1311 ms
2022-01-28 10:45:47.171 INFO 7939GG [main] o.s.s.c.ExecutorConfigurationSupport : Initializing ExecutorService 'applicationTaskExecutor'
2022-01-28 10:45:47.355 INFO 7939GG [main] o.s.s.c.ExecutorConfigurationSupport : Initializing ExecutorService 'taskScheduler'
2022-01-28 10:45:47.383 INFO 7939GG [main] o.a.j.l.DirectJDKLog : Starting ProtocolHandler ["http-nio-10999"]
2022-01-28 10:45:47.402 INFO 7939GG [main] o.s.b.w.e.t.TomcatWebServer : Tomcat started on port(s): 10999 (http) with context path '/middleware'
2022-01-28 10:45:47.414 INFO 7939GG [scheduling-1] c.a.m.f.j.CompassftJob : CompassftJob crawlData, start time is 10:45:47
2022-01-28 10:45:47.417 INFO 7939GG [main] o.s.b.StartupInfoLogger : Started testMain in 2.496 seconds (JVM running for 8.733)
adding as trusted cert:
....................
keyStore is :
keyStore type is : jks
keyStore provider is :
init keystore
init keymanager of type SunX509
trigger seeding of SecureRandom
done seeding SecureRandom
Allow unsafe renegotiation: false
Allow legacy hello messages: true
Is initial handshake: true
Is secure renegotiation: false
scheduling-1, setSoTimeout(0) called
scheduling-1, setSoTimeout(60000) called
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 for TLSv1
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_256_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384 for TLSv1
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 for TLSv1
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 for TLSv1.1
Ignoring unsupported cipher suite: TLS_RSA_WITH_AES_256_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 for TLSv1.1
Ignoring unsupported cipher suite: TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384 for TLSv1.1
Ignoring unsupported cipher suite: TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 for TLSv1.1
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 for TLSv1.1
%% No cached client session
update handshake state: client_hello[1]
upcoming handshake states: server_hello[2]
*** ClientHello, TLSv1.2
RandomCookie: GMT: 1626560475 bytes = { 112, 239, 236, 239, 122, 212, 244, 10, 144, 127, 175, 230, 81, 156, 57, 128, 83, 111, 76, 99, 217, 111, 179, 84, 241, 81, 103, 94 }
Session ID: {}
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384, TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384, TLS_DHE_RSA_WITH_AES_256_CBC_SHA256, TLS_DHE_DSS_WITH_AES_256_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA, TLS_RSA_WITH_AES_256_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDH_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_DSS_WITH_AES_256_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384, TLS_RSA_WITH_AES_256_GCM_SHA384, TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384, TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384, TLS_DHE_RSA_WITH_AES_256_GCM_SHA384, TLS_DHE_DSS_WITH_AES_256_GCM_SHA384, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
Extension elliptic_curves, curve names: {secp256r1, secp384r1, secp521r1}
Extension ec_point_formats, formats: [uncompressed]
Extension signature_algorithms, signature_algorithms: SHA512withECDSA, SHA512withRSA, SHA384withECDSA, SHA384withRSA, SHA256withECDSA, SHA256withRSA, SHA256withDSA, SHA224withECDSA, SHA224withRSA, SHA224withDSA, SHA1withECDSA, SHA1withRSA, SHA1withDSA
Extension extended_master_secret
Extension server_name, server_name: [type=host_name (0), value=api.compass-ft.com]
***
[write] MD5 and SHA1 hashes: len = 212
0000: 01 00 00 D0 03 03 61 F3 58 DB 70 EF EC EF 7A D4 ......a.X.p...z.
0010: F4 0A 90 7F AF E6 51 9C 39 80 53 6F 4C 63 D9 6F ......Q.9.SoLc.o
0020: B3 54 F1 51 67 5E 00 00 56 C0 24 C0 28 00 3D C0 .T.Qg^..V.$.(.=.
0030: 26 C0 2A 00 6B 00 6A C0 0A C0 14 00 35 C0 05 C0 &.*.k.j.....5...
0040: 0F 00 39 00 38 C0 23 C0 27 00 3C C0 25 C0 29 00 ..9.8.#.'.<.%.).
0050: 67 00 40 C0 09 C0 13 00 2F C0 04 C0 0E 00 33 00 g.@...../.....3.
0060: 32 C0 2C C0 2B C0 30 00 9D C0 2E C0 32 00 9F 00 2.,.+.0.....2...
0070: A3 C0 2F 00 9C C0 2D C0 31 00 9E 00 A2 00 FF 01 ../...-.1.......
0080: 00 00 51 00 0A 00 08 00 06 00 17 00 18 00 19 00 ..Q.............
0090: 0B 00 02 01 00 00 0D 00 1C 00 1A 06 03 06 01 05 ................
00A0: 03 05 01 04 03 04 01 04 02 03 03 03 01 03 02 02 ................
00B0: 03 02 01 02 02 00 17 00 00 00 00 00 17 00 15 00 ................
00C0: 00 12 61 70 69 2E 63 6F 6D 70 61 73 73 2D 66 74 ..api.compass-ft
00D0: 2E 63 6F 6D .com
scheduling-1, WRITE: TLSv1.2 Handshake, length = 212
[Raw write]: length = 217
0000: 16 03 03 00 D4 01 00 00 D0 03 03 61 F3 58 DB 70 ...........a.X.p
0010: EF EC EF 7A D4 F4 0A 90 7F AF E6 51 9C 39 80 53 ...z.......Q.9.S
0020: 6F 4C 63 D9 6F B3 54 F1 51 67 5E 00 00 56 C0 24 oLc.o.T.Qg^..V.$
0030: C0 28 00 3D C0 26 C0 2A 00 6B 00 6A C0 0A C0 14 .(.=.&.*.k.j....
0040: 00 35 C0 05 C0 0F 00 39 00 38 C0 23 C0 27 00 3C .5.....9.8.#.'.<
0050: C0 25 C0 29 00 67 00 40 C0 09 C0 13 00 2F C0 04 .%.).g.@...../..
0060: C0 0E 00 33 00 32 C0 2C C0 2B C0 30 00 9D C0 2E ...3.2.,.+.0....
0070: C0 32 00 9F 00 A3 C0 2F 00 9C C0 2D C0 31 00 9E .2...../...-.1..
0080: 00 A2 00 FF 01 00 00 51 00 0A 00 08 00 06 00 17 .......Q........
0090: 00 18 00 19 00 0B 00 02 01 00 00 0D 00 1C 00 1A ................
00A0: 06 03 06 01 05 03 05 01 04 03 04 01 04 02 03 03 ................
00B0: 03 01 03 02 02 03 02 01 02 02 00 17 00 00 00 00 ................
00C0: 00 17 00 15 00 00 12 61 70 69 2E 63 6F 6D 70 61 .......api.compa
00D0: 73 73 2D 66 74 2E 63 6F 6D ss-ft.com
[Raw read]: length = 5
0000: 16 03 03 00 37 ....7
[Raw read]: length = 55
0000: 02 00 00 33 03 03 94 62 C2 45 AD 7F 63 B8 F6 7C ...3...b.E..c...
0010: D4 D5 7A A7 89 AE AB FD F0 82 F9 22 21 15 44 4F ..z........"!.DO
0020: 57 4E 47 52 44 01 00 C0 2F 00 00 0B FF 01 00 01 WNGRD.../.......
0030: 00 00 0B 00 02 01 00 .......
scheduling-1, READ: TLSv1.2 Handshake, length = 55
check handshake state: server_hello[2]
*** ServerHello, TLSv1.2
RandomCookie: GMT: -1805532603 bytes = { 173, 127, 99, 184, 246, 124, 212, 213, 122, 167, 137, 174, 171, 253, 240, 130, 249, 34, 33, 21, 68, 79, 87, 78, 71, 82, 68, 1 }
Session ID: {}
# 注意到
生产上(失败):
trustStore is: /apps/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_ECDSA_WITH_RC4_128_SHA, TLS_ECDHE_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_SHA, TLS_ECDH_ECDSA_WITH_RC4_128_SHA, TLS_ECDH_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_MD5, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
dev上(成功):
trustStore is: /etc/pki/java/cacerts
ignore的都是 ***128-SHA
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384, TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384, TLS_DHE_RSA_WITH_AES_256_CBC_SHA256, TLS_DHE_DSS_WITH_AES_256_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA, TLS_RSA_WITH_AES_256_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA, TLS_ECDH_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_RSA_WITH_AES_256_CBC_SHA, TLS_DHE_DSS_WITH_AES_256_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384, TLS_RSA_WITH_AES_256_GCM_SHA384, TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384, TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384, TLS_DHE_RSA_WITH_AES_256_GCM_SHA384, TLS_DHE_DSS_WITH_AES_256_GCM_SHA384, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
# 查看一下服务器支持的TLS版本类型:
https://stackoverflow.com/questions/28908835/ssl-peer-shut-down-incorrectly-in-java
> nmap -p 443 --script ssl-enum-ciphers api.compass-ft.com
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-28 09:05 Malay Peninsula Standard Time
Nmap scan report for api.compass-ft.com (108.128.72.146)
Host is up (0.23s latency).
Other addresses for api.compass-ft.com (not scanned): 54.73.26.109 54.216.252.255
rDNS record for 108.128.72.146: ec2-108-128-72-146.eu-west-1.compute.amazonaws.com
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Forward Secrecy not supported by any cipher
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 10.33 seconds
貌似支持128和256
# dev上用的java跟生产上的不同
生产:
# java -version
openjdk version "1.8.0_40"
OpenJDK Runtime Environment (build 1.8.0_40-b25)
OpenJDK 64-Bit Server VM (build 25.40-b25, mixed mode)
dev:
# java -version
openjdk version "1.8.0_191"
OpenJDK Runtime Environment (build 1.8.0_191-b12)
OpenJDK 64-Bit Server VM (build 25.191-b12, mixed mode)
也没有很大差别,不过安装方式不同,可以看到前面输出两者使用的truststore不同,
dev用的是os的 trustStore is: /etc/pki/java/cacerts
生产用的是jre自己的 trustStore is: /apps/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts
试着用openjdk的cacerts请求一下,居然可以
[root@sgtcs-mdw-v02 test-datasource]# curl -v --capath /opt/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts https://api.compass-ft.com/v1/indexes/CCRTBTC/history?access_token=
* About to connect() to api.compass-ft.com port 443 (#0)
* Trying 54.73.26.109...
* Connected to api.compass-ft.com (54.73.26.109) port 443 (#0)
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* warning: CURLOPT_CAPATH not a directory (/opt/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts)
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: /opt/3rd-party/java-se-8u40-ri/jre/lib/security/cacerts
* SSL connection using TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
* Server certificate:
* subject: CN=api.compass-ft.com
* start date: Dec 09 23:25:14 2021 GMT
* expire date: Mar 09 23:25:13 2022 GMT
* common name: api.compass-ft.com
* issuer: CN=R3,O=Let's Encrypt,C=US
> GET /v1/indexes/CCRTBTC/history?access_token= HTTP/1.1
> User-Agent: curl/7.29.0
> Host: api.compass-ft.com
> Accept: */*
反过来用系统的ca给java程序试一下 #java -jar -Djavax.net.debug=all -Djavax.net.ssl.trustStore=/etc/pki/java/cacerts test-datasource.jar 仍然是不行
然后想到在dev上用生产的jdk版本试试,确实能够重现出错误!
openjdk-8u40-b25-linux-x64-10_feb_2015.tar.gz openjdk-8u41-b04-linux-x64-14_jan_2020.tar.gz 这两个版本都有问题,可能是这个版本的jdk底层实现的tls handshake采用的cipher suite已经过时了;
结合之前VAPT漏洞扫描遇到过的一个tls hardening的问题,我觉着也有可能: 因为这个版本的jdk刚好优先使用了os所支持的某些比较不安全的cipher suite,然后compassft服务端对这些不安全的算法进行了屏蔽,所以另一种可能的解决办法是对os进行tls hardening可能可以解决这个问题
# java.security
想到是否可以通过更改java security配置来修复这个问题:
Additional information on Oracle's JDK and JRE Cryptographic Algorithms https://java.com/en/configure_crypto.html
[root@sgtcs-mdw-v02 java-se-8u40-ri]# grep -r -l "cipher" ./*
./jre/lib/security/java.security
./jre/lib/rt.jar
./jre/lib/jsse.jar
./jre/lib/management/management.properties
./jre/lib/amd64/server/libjvm.so
./lib/ct.sym
./man/ja_JP.UTF-8/man1/keytool.1
./man/man1/keytool.1
./sample/jmx/jmx-scandir/src/etc/management.properties
参照dev上面的java.security配置,更改了生产,
也试了jvm参数 java -jar -Djavax.net.debug=all -Djdk.tls.client.cipherSuites=TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 test-datasource.jar
不过没有解决,两种可能:
一种可能是有些配置只是对当前的程序是server端有效,而我现在是client端;
另一种可能是jdk处理握手的代码有hardcode https://github.com/AdoptOpenJDK/openjdk-jdk8u/blob/master/jdk/src/share/classes/sun/security/ssl/CipherSuite.java
# jdk9也不行
JDK 9好像握手能够进行多几步了,但是居然爆了另外一个错误:
System property jdk.tls.client.cipherSuites is set to 'null'
System property jdk.tls.server.cipherSuites is set to 'null'
scheduling-1, handling exception: java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
%% Invalidated: [Session-5, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256]
scheduling-1, SEND TLSv1.2 ALERT: fatal, description = internal_error
scheduling-1, WRITE: TLSv1.2 Alert, length = 2
[Raw write]: length = 7
0000: 15 03 03 00 02 02 50 ......P
scheduling-1, called closeSocket()
scheduling-1, called close()
scheduling-1, called closeInternal(true)
scheduling-1, called closeSocket()
scheduling-1, called close()
scheduling-1, called closeInternal(true)
scheduling-1, called close()
scheduling-1, called closeInternal(true)
2022-01-31 12:05:52.181 ERROR 21924GG [scheduling-1] c.a.m.f.u.HttpClientUtil : Get Exception java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
javax.net.ssl.SSLException: java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
at java.base/sun.security.ssl.Alerts.getSSLException(Alerts.java:214)
at java.base/sun.security.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1969)
at java.base/sun.security.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1921)
at java.base/sun.security.ssl.SSLSocketImpl.handleException(SSLSocketImpl.java:1904)
at java.base/sun.security.ssl.SSLSocketImpl.handleException(SSLSocketImpl.java:1830)
at java.base/sun.security.ssl.AppOutputStream.write(AppOutputStream.java:71)
at java.base/java.io.BufferedOutputStream.flushBuffer(BufferedOutputStream.java:81)
at java.base/java.io.BufferedOutputStream.flush(BufferedOutputStream.java:142)
at org.apache.commons.httpclient.HttpConnection.flushRequestOutputStream(HttpConnection.java:828)
at org.apache.commons.httpclient.HttpMethodBase.writeRequest(HttpMethodBase.java:2116)
at org.apache.commons.httpclient.HttpMethodBase.execute(HttpMethodBase.java:1096)
at org.apache.commons.httpclient.HttpMethodDirector.executeWithRetry(HttpMethodDirector.java:398)
at org.apache.commons.httpclient.HttpMethodDirector.executeMethod(HttpMethodDirector.java:171)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:397)
at org.apache.commons.httpclient.HttpClient.executeMethod(HttpClient.java:323)
at com.lyhistory.middleware.test.util.HttpClientUtil.sendGet(HttpClientUtil.java:64)
at com.lyhistory.middleware.test.service.impl.CompassftServiceImpl.sendRequest(CompassftServiceImpl.java:25)
at com.lyhistory.middleware.test.job.CompassftJob.crawlData(CompassftJob.java:33)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:564)
at org.springframework.scheduling.support.ScheduledMethodRunnable.run(ScheduledMethodRunnable.java:84)
at org.springframework.scheduling.support.DelegatingErrorHandlingRunnable.run(DelegatingErrorHandlingRunnable.java:54)
at java.base/java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:514)
at java.base/java.util.concurrent.FutureTask.runAndReset(FutureTask.java:305)
at java.base/java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:300)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1167)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:641)
at java.base/java.lang.Thread.run(Thread.java:844)
Caused by: java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
at java.base/sun.security.validator.PKIXValidator.<init>(PKIXValidator.java:89)
at java.base/sun.security.validator.Validator.getInstance(Validator.java:181)
at java.base/sun.security.ssl.X509TrustManagerImpl.getValidator(X509TrustManagerImpl.java:330)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrustedInit(X509TrustManagerImpl.java:180)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:192)
at java.base/sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:133)
at java.base/sun.security.ssl.ClientHandshaker.checkServerCerts(ClientHandshaker.java:1825)
at java.base/sun.security.ssl.ClientHandshaker.serverCertificate(ClientHandshaker.java:1655)
at java.base/sun.security.ssl.ClientHandshaker.processMessage(ClientHandshaker.java:260)
at java.base/sun.security.ssl.Handshaker.processLoop(Handshaker.java:1086)
at java.base/sun.security.ssl.Handshaker.processRecord(Handshaker.java:1020)
at java.base/sun.security.ssl.SSLSocketImpl.processInputRecord(SSLSocketImpl.java:1137)
at java.base/sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1074)
at java.base/sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:973)
at java.base/sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1402)
at java.base/sun.security.ssl.SSLSocketImpl.writeRecord(SSLSocketImpl.java:733)
at java.base/sun.security.ssl.AppOutputStream.write(AppOutputStream.java:67)
... 24 more
Caused by: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
at java.base/java.security.cert.PKIXParameters.setTrustAnchors(PKIXParameters.java:200)
at java.base/java.security.cert.PKIXParameters.<init>(PKIXParameters.java:120)
at java.base/java.security.cert.PKIXBuilderParameters.<init>(PKIXBuilderParameters.java:104)
at java.base/sun.security.validator.PKIXValidator.<init>(PKIXValidator.java:86)
... 40 more
中间还找到类似的bug https://bugs.openjdk.java.net/browse/JDK-8266562
可以看到有的bug同时出现在多个版本,所以高版本的某个小版本可能并没有低版本的fix,
# openjdk8 update
所以继续找openjdk8u191,没找到,只找到Oracle和redhat编译的,试了下Oracle的果然没问题
https://www.oracle.com/java/technologies/javase/javase8-archive-downloads.html
https://www.oracle.com/java/technologies/javase/8u191-relnotes.html
https://developers.redhat.com/products/openjdk/download
最后找到openjdk的8u系列的版本:
openjdk build 1.8.0_191-b12 openjdk site=> left panel click "java 8 update"=> click "wiki" https://openjdk.java.net/projects/jdk8u/ =》 https://wiki.openjdk.java.net/display/jdk8u Note:
http://hg.openjdk.java.net/jdk8u/jdk8u/ 滚动到下面看到 Added tag jdk8u191-b12 for changeset 6432b2dd408cjdk8u191-b26
虽然没有8u191的release,测试了8u的最高版本8u312b07,果然成功了!
没有尝试的可能方案:
HttpClient如何指定CipherSuites https://ask.csdn.net/questions/189433 en.setEnabledCipherSuites(new String[]{"TLS_RSA_WITH_AES_128_CBC_SHA"});
# 解决之后研究原因
https://bugs.openjdk.java.net/browse/JDK-8144544?jql=text%20~%20%22%5C%22Remote%20host%20closed%20connection%20during%20handshake%5C%22%22
https://bugs.openjdk.java.net/browse/JDK-8144544
看来这个比较像,有可能是interoperability issue
Check for alternate AES providers. If there's a bad provider, the peer could easily result in a bad padding.
The submitter's environment may have been using IBM JDK and trying to use Oracle's keymanager SunX509 implementation. No further updates. Closing out as not an issue.
openjdk ibm padding EOFException handshake
https://www.ibm.com/support/pages/apar/IV37231
The problem happens because the size of the "PreMaster Secret" generated from ECDH KeyAgreement in IBMJCE provider did not match openssl's counterpart for some of the EC curves.
https://wiki.openjdk.java.net/display/jdk8u
下载代码,确实有很多相关的修复
git clone https://github.com/openjdk/jdk8u
cd jdk8u/
git status
git tag
git checkout jdk8u40-b25
git checkout jdk8u191-b12
git log -S"receiveChangeCipherSpec"
git log -S"receiveChangeCipherSpec"
git show b9d40c7d6cfa8f221bf1973821b97210e6f3a5be
git log -S"provider"
GIT SHOW b380264de3d82ceb291401dae06e9c605e36ebd0
git show b380264de3d82ceb291401dae06e9c605e36ebd0
git log -S"padding"
git log -S"ECDH"
git log -S"EC curve"
# 跟上一个问题本质一样:Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
maven 报错: [ERROR] Plugin org.apache.maven.plugins:maven-clean-plugin:2.5 or one of its dependencies could not be resolved: Failed to read artifact descriptor for org.apache.maven.plugins:maven-clean-plugin:jar:2.5: Could not transfer artifact org.apache.maven.plugins:maven-clean-plugin:pom:2.5 from/to central (https://repo.maven.apache.org/maven2): java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
刚开始怀疑是ca找不到,所以指定了path:
mvn clean install -Djavax.net.ssl.trustStore="%JAVA_HOME%/jre/lib/security/cacerts"
一样报错
执行:
keytool -printcert -sslserver https://repo.maven.apache.org/maven2
报错:keytool error: java.lang.Exception: No certificate from the SSL server
然后就以为仅仅是没有安装好cert(后来发现上面命令写错,应该是 keytool -printcert -sslserver repo.maven.apache.org:443/maven2),所以用openssl下载
openssl s_client -showcerts -connect https://repo.maven.apache.org/maven2
报错:getservbyname failure,原来是命令写错了,不能用url,因为
As SSL is an TCP-level protocol rather than HTTP, strip the protocol and path from the -connect to make that command work: 改正:
openssl s_client -showcerts -connect repo.maven.apache.org:443/maven2继续报错: Loading 'screen' into random state - done CONNECTED(000003B8) 36464:error:1407742E:SSL routines:SSL23_GET_SERVER_HELLO:tlsv1 alert protocol version:.\ssl\s23_clnt.c:596:
看到tlsv1,很陈旧了,怪不得不行
Java releases < JDK 8 As noted in this blog post by Oracle, TLSv1 was used by default for JDK releases prior to JDK 8. JDK 8 changed this behavior and defaults to TLSv1.2. Any client (ex. JGit is one such popular client) that runs on older versions of the JDK is affected. This can be addressed by updating to JDK >= 8 or explicitly opting in to TLSv1.2 in JDK 7 (look at the https.protocols JSSE tuning parameter). Unfortunately, versions of the JDK <= 6 do not support TLSv1.2. We advise users of JDK <= 6 to upgrade to a newer version of the JDK.
maven或者maven作为java工具使用的jdk到底是什么tls版本呢,这才想起可以用debug模式嘛!
>mvn clean -Djavax.net.debug=ssl:handshake:verbose
[INFO] Scanning for projects...
[INFO]
[INFO] --------------------< ngs.apex.com:ngs-kafka-redis >--------------------
[INFO] Building ngs-kafka-redis 1.0-SNAPSHOT
[INFO] --------------------------------[ jar ]---------------------------------
keyStore is :
keyStore type is : jks
keyStore provider is :
init keystore
init keymanager of type SunX509
trustStore is: C:\Program Files\Java\openjdk-8u42-b03-windows-i586-14_jul_2022\java-se-8u42-ri\jre\lib\security\cacerts
trustStore type is : jks
trustStore provider is :
init truststore
trigger seeding of SecureRandom
done seeding SecureRandom
Downloading from central: https://repo.maven.apache.org/maven2/org/apache/maven/plugins/maven-clean-plugin/2.5/maven-clean-plugin-2.5.pom
Ignoring unavailable cipher suite: TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
...........................
Ignoring unavailable cipher suite: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
Allow unsafe renegotiation: false
Allow legacy hello messages: true
Is initial handshake: true
Is secure renegotiation: false
Ignoring unsupported cipher suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 for TLSv1
...........................
Ignoring unsupported cipher suite: TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 for TLSv1.1
%% No cached client session
*** ClientHello, TLSv1.2
RandomCookie: GMT: 1698637036 bytes = { 209, 36, 180, 104, 123, 125, 185, 208, 135, 243, 5, 246, 5, 4, 149, 203, 38, 227, 243, 114, 209, 160, 154, 44, 98, 64, 216, 237 }
Session ID: {}
Cipher Suites: [TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_RSA_WITH_AES_128_CBC_SHA256, TLS_DHE_DSS_WITH_AES_128_CBC_SHA256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA, TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA, TLS_ECDH_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_RSA_WITH_AES_128_CBC_SHA, TLS_DHE_DSS_WITH_AES_128_CBC_SHA, TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, TLS_RSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256, TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_RSA_WITH_AES_128_GCM_SHA256, TLS_DHE_DSS_WITH_AES_128_GCM_SHA256, TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA, TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA, SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA, TLS_ECDHE_ECDSA_WITH_RC4_128_SHA, TLS_ECDHE_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_SHA, TLS_ECDH_ECDSA_WITH_RC4_128_SHA, TLS_ECDH_RSA_WITH_RC4_128_SHA, SSL_RSA_WITH_RC4_128_MD5, TLS_EMPTY_RENEGOTIATION_INFO_SCSV]
Compression Methods: { 0 }
Extension elliptic_curves, curve names: {secp256r1, sect163k1, sect163r2, secp192r1, secp224r1, sect233k1, sect233r1, sect283k1, sect283r1, secp384r1, sect409k1, sect409r1, secp521r1, sect571k1, sect571r1, secp160k1, secp160r1, secp160r2, sect163r1, secp192k1, sect193r1, sect193r2, secp224k1, sect239k1, secp256k1}
Extension ec_point_formats, formats: [uncompressed]
Extension signature_algorithms, signature_algorithms: SHA512withECDSA, SHA512withRSA, SHA384withECDSA, SHA384withRSA, SHA256withECDSA, SHA256withRSA, SHA224withECDSA, SHA224withRSA, SHA1withECDSA, SHA1withRSA, SHA1withDSA, MD5withRSA
Extension server_name, server_name: [type=host_name (0), value=repo.maven.apache.org]
***
main, WRITE: TLSv1.2 Handshake, length = 237
main, READ: TLSv1.2 Handshake, length = 91
*** ServerHello, TLSv1.2
RandomCookie: GMT: 1698637036 bytes = { 11, 26, 138, 205, 219, 12, 47, 76, 81, 250, 116, 198, 4, 121, 217, 252, 16, 77, 103, 11, 173, 27, 249, 11, 188, 241, 110, 114 }
Session ID: {243, 233, 42, 175, 111, 215, 73, 173, 200, 132, 149, 173, 131, 151, 65, 120, 8, 240, 32, 245, 220, 99, 53, 59, 216, 248, 138, 37, 220, 224, 226, 29}
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
Compression Method: 0
Extension server_name, server_name:
Extension renegotiation_info, renegotiated_connection: <empty>
Extension ec_point_formats, formats: [uncompressed]
***
%% Initialized: [Session-1, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256]
** TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
main, READ: TLSv1.2 Handshake, length = 2831
*** Certificate chain
chain [0] = [
[
Version: V3
Subject: CN=repo.maven.apache.org
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
params: null
modulus: 28795882934893170709623103651489185786975131948609576963107688434511348310799802656845161034643210777058995329074431904764998037079985935160874251932529088221962175039191746870936504441381816177009381056896033366380084462000778878049779150489872742696438528007493098911402774939286666937972636658579084418254399343610870831413603481932550983328398869983159007061407084769194187816409958865599623151601605308929809745759759171345763173435175230826903492910465231908482466346877446616723920841555903920739078053322860422933292965497520565842570224994296029712905922877471944410263027535162063433759545525713408812439991
public exponent: 65537
Validity: [From: Thu Mar 16 01:45:12 SGT 2023,
To: Tue Apr 16 01:45:11 SGT 2024]
Issuer: CN=GlobalSign Atlas R3 DV TLS CA 2023 Q1, O=GlobalSign nv-sa, C=BE
SerialNumber: [ 01035f98 55d9b4b4 33feec3b 9fd3dc3b]
Certificate Extensions: 10
[1]: ObjectId: 1.3.6.1.4.1.11129.2.4.2 Criticality=false
Extension unknown: DER encoded OCTET string =
0000: 04 82 01 6C 04 82 01 68 01 66 00 75 00 76 FF 88 ...l...h.f.u.v..
0010: 3F 0A B6 FB 95 51 C2 61 CC F5 87 BA 34 B4 A4 CD ?....Q.a....4...
0020: BB 29 DC 68 42 0A 9F E6 67 4C 5A 3A 74 00 00 01 .).hB...gLZ:t...
0030: 86 E6 60 3F 62 00 00 04 03 00 46 30 44 02 20 37 ..`?b.....F0D. 7
0040: 23 0A 06 44 D3 43 E8 1A 8B 51 8E DB DB 79 EA 42 #..D.C...Q...y.B
0050: ED 01 D4 3E 55 B5 13 EA 4A C1 0D A2 7A 2D 95 02 ...>U...J...z-..
0060: 20 26 7B 0D 1C A8 AE 90 F9 F6 31 15 68 85 3D C9 &........1.h.=.
0070: CE EB 50 06 F0 5E 02 B3 84 7C 60 9A D8 D6 8A 53 ..P..^....`....S
0080: 26 00 76 00 3B 53 77 75 3E 2D B9 80 4E 8B 30 5B &.v.;Swu>-..N.0[
0090: 06 FE 40 3B 67 D8 4F C3 F4 C7 BD 00 0D 2D 72 6F ..@;g.O......-ro
00A0: E1 FA D4 17 00 00 01 86 E6 60 3F 88 00 00 04 03 .........`?.....
00B0: 00 47 30 45 02 21 00 C8 5A BE DF A4 5F 1A 20 36 .G0E.!..Z..._. 6
00C0: 72 99 5A C8 55 7C 68 82 B5 C1 26 11 20 C1 CE 66 r.Z.U.h...&. ..f
00D0: D6 EC F7 30 73 D8 0E 02 20 35 95 17 8A DE F9 37 ...0s... 5.....7
00E0: 20 54 57 A4 13 3B EA 4A F7 3F 0B C3 E7 B1 0F 95 TW..;.J.?......
00F0: B2 70 61 42 D5 9B 35 C9 1B 00 75 00 DA B6 BF 6B .paB..5...u....k
0100: 3F B5 B6 22 9F 9B C2 BB 5C 6B E8 70 91 71 6C BB ?.."....\k.p.ql.
0110: 51 84 85 34 BD A4 3D 30 48 D7 FB AB 00 00 01 86 Q..4..=0H.......
0120: E6 60 3F D0 00 00 04 03 00 46 30 44 02 20 58 4D .`?......F0D. XM
0130: FA 1B 6A 97 8E FA CA CE 13 8B 74 B8 28 AA 24 7F ..j.......t.(.$.
0140: 6B B3 E1 F4 6B 1C B2 27 8A A3 F3 05 45 68 02 20 k...k..'....Eh.
0150: 05 B7 90 28 E1 7D FF CF 43 59 10 64 E6 14 64 CD ...(....CY.d..d.
0160: 03 2D E4 2F 2C 76 24 78 19 07 D7 B2 03 40 E1 57 .-./,[email protected]
[2]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://ocsp.globalsign.com/ca/gsatlasr3dvtlsca2023q1
,
accessMethod: caIssuers
accessLocation: URIName: http://secure.globalsign.com/cacert/gsatlasr3dvtlsca2023q1.crt
]
]
[3]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 4A EE A2 47 63 43 3B 3E 78 F3 B4 61 83 72 88 7A J..GcC;>x..a.r.z
0010: 9D E4 BD B7 ....
]
]
[4]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
[5]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.globalsign.com/ca/gsatlasr3dvtlsca2023q1.crl]
]]
[6]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.4146.10.1.3]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 26 68 74 74 70 73 3A 2F 2F 77 77 77 2E 67 6C .&https://www.gl
0010: 6F 62 61 6C 73 69 67 6E 2E 63 6F 6D 2F 72 65 70 obalsign.com/rep
0020: 6F 73 69 74 6F 72 79 2F ository/
]] ]
]
[7]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[8]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
[9]: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: repo.maven.apache.org
]
[10]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: A2 41 82 30 FD 20 1E AD 6E C5 F5 60 C5 49 DA 6B .A.0. ..n..`.I.k
0010: 65 F1 03 E7 e...
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 04 25 62 42 2D 7D D5 DD 6F 15 12 7F B0 6E 56 9A .%bB-...o....nV.
0010: 17 9E 75 E7 E9 19 69 BC 42 69 09 36 10 B4 BA DB ..u...i.Bi.6....
0020: EE A3 4B 70 FB 45 69 05 9C BB CB D4 48 87 BB D0 ..Kp.Ei.....H...
0030: 45 B4 36 F9 66 EC C6 D8 72 16 CA 6A 10 99 18 3C E.6.f...r..j...<
0040: EC 68 53 C3 55 DC C7 1C AF 35 8E D0 FB AF 3E 4E .hS.U....5....>N
0050: EB A8 22 68 84 7B D9 29 E6 DB 3A E1 2F E4 FC 7B .."h...)..:./...
0060: A1 DB AC C1 B3 1C 4D 18 2D FA A4 21 F4 FB 46 4B ......M.-..!..FK
0070: D0 1F 5E F9 B9 C5 C6 9E 57 9B 18 C9 CF B5 47 04 ..^.....W.....G.
0080: 57 89 0B 7D 7C C3 D7 B3 D7 FF F2 DF F8 D2 93 CB W...............
0090: 68 EC FE D3 91 AF C6 4C D3 5C 44 D2 14 2F 41 C7 h......L.\D../A.
00A0: F6 26 C8 CA FE F2 03 10 D6 82 98 86 27 92 C8 8D .&..........'...
00B0: 47 FC 15 88 26 91 E1 E9 05 6B E5 BE A3 1B A5 45 G...&....k.....E
00C0: FE 89 44 B0 FF 72 9A 8A 16 29 E4 6C 3B 58 A2 B6 ..D..r...).l;X..
00D0: BD 52 E3 5C A2 F0 B7 88 46 4C 13 43 79 E3 20 FF .R.\....FL.Cy. .
00E0: 30 4F A4 21 65 86 BC AE 55 48 EC 49 C9 7C BC 0F 0O.!e...UH.I....
00F0: CF A5 51 89 61 CE 3B 77 2D 12 AB EE 53 E2 24 D0 ..Q.a.;w-...S.$.
]
chain [1] = [
[
Version: V3
Subject: CN=GlobalSign Atlas R3 DV TLS CA 2023 Q1, O=GlobalSign nv-sa, C=BE
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
params: null
modulus: 22941182395348209119228249726660887858982599495232930369943940778119370598005314768543184682686715394486071593426418166888450349001350102649337188343001416419398052557334306738847492388373635574320259007569262959914518081798822155847737418641363799800748857854899290714685301338337310532066938363767866421215369791882818989684086341799298031628895579924634179196014833310804027217895253579752528603133597659946455003267832674856984788115576493236293338336856286111413325485730798313857421555414130349520016887608182648469835491249743188502481439641920200126892980772957171158548827169732281195247623293620193847883027
public exponent: 65537
Validity: [From: Wed Oct 12 11:48:28 SGT 2022,
To: Sat Oct 12 08:00:00 SGT 2024]
Issuer: CN=GlobalSign, O=GlobalSign, OU=GlobalSign Root CA - R3
SerialNumber: [ 7d4d424a 0bd1ed1a 3512a8e2 4955356c]
Certificate Extensions: 8
[1]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://ocsp2.globalsign.com/rootr3
,
accessMethod: caIssuers
accessLocation: URIName: http://secure.globalsign.com/cacert/root-r3.crt
]
]
[2]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 8F F0 4B 7F A8 2E 45 24 AE 4D 50 FA 63 9A 8B DE ..K...E$.MP.c...
0010: E2 DD 1B BC ....
]
]
[3]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:0
]
[4]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.globalsign.com/root-r3.crl]
]]
[5]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.4146.10.1.3]
[] ]
]
[6]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[7]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
[8]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 4A EE A2 47 63 43 3B 3E 78 F3 B4 61 83 72 88 7A J..GcC;>x..a.r.z
0010: 9D E4 BD B7 ....
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 8A D1 05 04 09 3F 63 E0 66 75 4F 73 B0 58 FF E5 .....?c.fuOs.X..
0010: D1 EB 74 C8 D4 EE DB 3B 51 9F 2F 01 D5 20 F8 85 ..t....;Q./.. ..
0020: 5F 43 9F BC F7 16 D5 C3 44 39 F2 A0 0B 2F D8 34 _C......D9.../.4
0030: CD E5 E5 E0 C2 B3 0A DA 7D 10 65 BC 83 91 B2 54 ..........e....T
0040: 6B 10 06 7E 3A 4D 1C 78 09 FD 8A 3C BB E2 6C A6 k...:M.x...<..l.
0050: D0 C3 46 E7 48 6B 12 36 C4 E8 28 19 15 58 92 1D ..F.Hk.6..(..X..
0060: 17 37 31 38 E7 CD F4 71 80 B0 8E 7A 9E 1E 83 0F .718...q...z....
0070: 7C 27 F4 DE D8 61 86 6F 2A C4 39 46 A4 FF 25 31 .'...a.o*.9F..%1
0080: B2 80 24 81 02 2C C1 03 62 9E 13 19 93 60 39 A2 ..$..,..b....`9.
0090: 98 E7 14 01 BF 75 86 4C 61 04 95 AC B6 2B E4 53 .....u.La....+.S
00A0: 6D B5 B4 21 8E 6D D6 81 46 1B 50 F5 BC 3C 27 77 m..!.m..F.P..<'w
00B0: 98 D5 93 DA F9 19 09 66 55 2C A6 DF 02 21 11 B3 .......fU,...!..
00C0: D7 95 E7 06 2C DA F4 0E E0 43 24 A3 1B 88 97 FB ....,....C$.....
00D0: FF FD 3B 8F 61 A3 6E 24 33 93 37 AD 06 82 D0 02 ..;.a.n$3.7.....
00E0: 0A 45 80 3A 42 00 91 C6 A0 B1 5C BE B1 1E 80 AF .E.:B.....\.....
00F0: F5 6D CC D9 6C 8C 2D C7 39 7B 6D 3B AC B9 96 1A .m..l.-.9.m;....
]
***
main, handling exception: java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty
%% Invalidated: [Session-1, TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256]
main, SEND TLSv1.2 ALERT: fatal, description = internal_error
main, WRITE: TLSv1.2 Alert, length = 2
main, called closeSocket()
[INFO] ------------------------------------------------------------------------
[INFO] BUILD FAILURE
[INFO] ------------------------------------------------------------------------
[INFO] Total time: 3.273 s
[INFO] Finished at: 2023-10-30T11:41:33+08:00
[INFO] ------------------------------------------------------------------------
[ERROR] Plugin org.apache.maven.plugins:maven-clean-plugin:2.5 or one of its dependencies could not be resolved: Failed to read artifact descriptor for org.apache.maven.plugins:maven-clean-plugin:jar:2.5: Could not transfer artifact org.apache.maven.plugins:maven-clean-plugin:pom:2.5 from/to central (https://repo.maven.apache.org/maven2): java.lang.RuntimeException: Unexpected error: java.security.InvalidAlgorithmParameterException: the trustAnchors parameter must be non-empty -> [Help 1]
[ERROR]
[ERROR] To see the full stack trace of the errors, re-run Maven with the -e switch.
[ERROR] Re-run Maven using the -X switch to enable full debug logging.
[ERROR]
[ERROR] For more information about the errors and possible solutions, please read the following articles:
[ERROR] [Help 1] http://cwiki.apache.org/confluence/display/MAVEN/PluginResolutionException
这不就是跟前面一样的问题了,果断升级openjdk
# 根源
lib/security/cacerts内某个root证书过期
I manage manually my jdk and was getting this error with openjdk-8. I replaced the cacerts with the one of the openjdk-11 and it worked just fine. If you try this, make sure to backup your cacerts first.
另一种方法绕过: mvn clean -Dmaven.wagon.http.ssl.insecure=true -Dmaven.wagon.http.ssl.allowall=true
# outdated TLS1.0 - win10 打不开应用商店 Microsoft store
用“win + R”打开运行, 输入 inetcpl.cpl 打开Internet属性(或从IE浏览器设置打开),点击高级选项, 找到并勾选 TLS 1.2,取消勾选TLS 1.0
# CertificateException: No subject alternative names present
When the server certificate is having Subject Alternative Names (SAN), the requesting home name must match with one of the SANs. If the server’s SSL certificate does not have SANs, then the requesting home name must match with the Common Name (CN) of the certificate. https://stackoverflow.com/questions/29157861/java-certificateexception-no-subject-alternative-names-matching-ip-address
# 一些有意思的问题
Netty SSL性能调优 (opens new window) OPENSSL 知多少? https://mp.weixin.qq.com/s/QW-uO4OzSRtSkpI4LjGUQw 用jmeter通过ssl验证访问https https://cloud.tencent.com/developer/article/1199237?from=15425 解决 HTTPS 证书失效菜刀连不上 https://cloud.tencent.com/developer/article/1399952?from=15425 How can I disable a TLS cipher for only some protocols using JVM Config? https://stackoverflow.com/questions/52779312/java-how-can-i-disable-a-tls-cipher-for-only-some-protocols-using-jvm-config?rq=1
Comparative study of TLS Cipher Suite supported by Java 8 https://linuxtut.com/en/877120a7dfa9e4a0e1e3/